First attempted theft of customer vehicle
As a business providing GPS tracking and immobilisation, it was always only going to be a matter of time before a customer’s vehicle was hit with a theft attempt.
Even though our branding tends to focus on post-theft remote vehicle shutdown (aka “Safe Engine Cut Off” / SECO), this Monday the 24th of February, one of our customers had a theft attempt made on his VF Commodore SV6 Sportswagon while it was parked, with the vehicle immobilised using our harness. The usual - and still surprising - factors were at play:
Broad Daylight
Mere minutes after the car was supervised
Mere minutes before the owner came back out to their car
Security footage of the site (it was a work carpark) showed the thief arriving in another stolen VF Commodore, parking next to our customer and performing the standard attack against VF Commodores. First they used a box cutter on the wheel arch liner to access the horn wires.
Wheel arch liner cut with sharp knife.
Next, the thief cut the horn wires. This allows them to break into the vehicle without the alarm (the horn) sounding.
Stock horn wire location - cut by the thief.
To access the car, the thief then forced the driver’s door lock. Unfortunately there is little we can do as an immobiliser provider to alert before this event occurs, which is why we also recommend installing a horn relocation kit or even a dummy horn wire which triggers an audible alarm if the wires are cut.
Forced door lock. We are personally surprised that the door lock can be forced so easily.
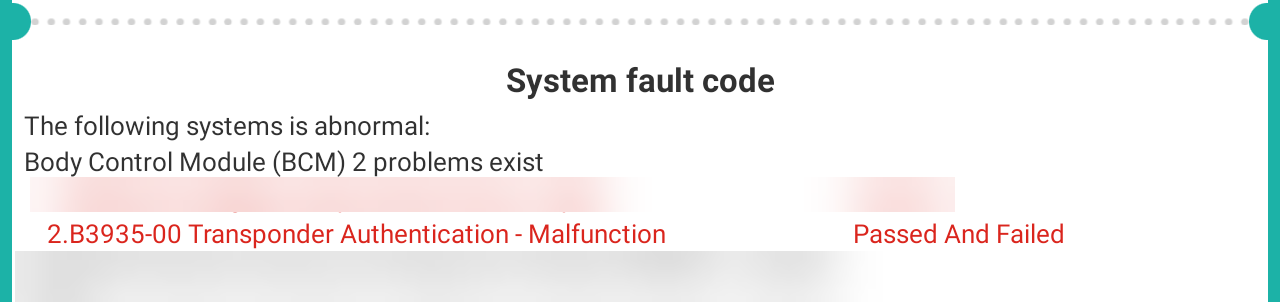
Finally, the thief accesses the vehicle and attempts to reprogram keys. This is where our immobiliser steps in. Keys in the VF Commodore are stored/registered in the Body Control Module (BCM) computer, but key reprogramming requires authentication between the BCM and the Engine Control Module (ECM / ECU). This authentication attempt fails because the ECU remains offline.
A subsequent diagnostic log dump from the targeted vehicle shows the thief’s attempts to program new keys failing.
Error codes registered in BCM when thieves attempt to program new keys with our immobiliser active.
Post Incident Review
As a service provider for stopping vehicle theft, or vehicle recovery in the event of a theft, we of course see this as very positive for us directly. However, our customer still had a wallet stolen from the vehicle and has had to deal with the ramifications of that.
We recommend that our service is always backed up by some kind of audible alert to reduce the time that a thief may have access to your vehicle. We are, perhaps, not the first line of defense, and indeed if you do forget to immobilise your vehicle and the thief makes off with it, we are absolutely the last line of defense due to our remote vehicle shutdown capability.
Our recommendations, particularly for VF Commodore owners are therefore:
Don’t leave valuables in your car. We can stop your vehicle being taken, but not your items within it.
Install a horn relocation, with consideration for a dummy horn wire that triggers an alarm if and when it is cut by a thief.
Consider warning stickers (we will also print and provide our own in future) so that thieves are aware they’re about to be thwarted. It won’t stop all thieves, but it may help reduce the total damage caused during a theft attempt.
Consider asking about our automatic immobilisation feature, to reduce the chance of your car being taken if you forget to disable the car.
Addendum: What if the thief had been able to program new keys?
It’s important to state that even if new keys had been successfully programmed, the vehicle would still not have started due to the ECU being offline.
However, there are thousands of vehicles on the market, and some of them have worse key security than others, where it may be possible to program new keys even with our immobilizer fitted. The worst case scenario here would be that your car doesn’t get taken but you can’t start it because your own keys have been erased from the system. Again, depending on the vehicle, that may be possible (although, thankfully, not for the VF Commodore). Key programming “in the field” by a mobile locksmith can cost upwards of $500, so it is best avoided.
As we build our business and install on newer vehicles, we check to determine whether the vehicle model is vulnerable to a key reprogram attack, and we will note this on our website. If a vehicle is vulnerable, we recommend additional protection such as an OBD2 port lock or port relocation. We don’t recommend advice that switches pins around on your OBD port; whilst frying a thief’s programming tool sounds great, then next time you take your car in for a service you will fry the $10,000 diagnostics tool used by the technicians there. You really don’t want to put yourself in a position of liability for damages.